What Is A Brute Force Attack complete guide will be described in this article.The greatest passwords are lengthy, complicated, and devoid of common keywords or basic names. This is due to the fact that simple or short passwords are easily cracked by a brute force attack. However, what is a brute force attack specifically? Learn how to defend yourself from brute force assaults and how a robust cyber security solution may assist.
What Is A Brute Force Attack?
In this article, you can know about What Is A Brute Force Attack here are the details below;
What is a brute force attack, exactly?
When hackers attempt to break a password by extensive trial and error with the use of a computer, it’s known as a brute force attack. With the advancement of computer technology, the definition and application of brute force have expanded.
This Article Contains:
- Exactly what is a brute force attack?
- various forms of forceful attack
- Equipment for applying brute force strikes
- Why are brute force assaults used by cybercriminals?
- How to ward off an assault with brute force
- Use Avast One to defend against brute force assaults.
A hacker could only potentially attempt thousands of different password combinations every second in the 1970s. There are hundreds of billions of login attempts possible every second with contemporary computing.
The concept of brute force has broadened, but the approach is the same: attempt a large number of password combinations in the hopes that one will work. The amount of time and resources an attacker is willing to invest determines whether or not they are successful in figuring out the password. But what techniques do hackers of today employ?
Types of brute force attack
Brute force attacks can be broadly classified into five categories: reverse attacks, dictionary attacks, hybrid attacks, basic attacks, and credential stuffing. A brute force decryption tool is a sort of software that conducts brute force attacks automatically, and it may be obtained by anyone with a little interest in technology.
Brute force tools are typically used to crack passwords and decrypt databases of stolen credentials. The computer power and available resources of the people who created a brute force instrument determine its usefulness.
It’s possible that the average lone-wolf bedroom hacker lacks the funds to purchase an extremely powerful machine capable of breaking passwords. However, the meaning of a hacker has evolved over time. These days, a large number of cybercriminals are part of well-funded, highly structured groups that have access to the best password cracking methods available.
Simple brute force attacks
Basic brute force attacks don’t require much creativity or processing capacity. Until they succeed, they methodically cycle through word, letter, and character combinations. Simple assaults usually target variations of the most popular or likely passwords; they cannot crack long or complex passwords.
It is possible to manually do a basic brute force attack, however it will take a lot more time. A predictable password is easily brute-forced by a bot. For this reason, some of the worst passwords are just a string of consecutive numbers (123456), someone’s name or birthday, or the infamous—yet surprisingly popular—”password.”
Simple brute force attacks are designed to guess weak passwords by repeatedly trying different word and number combinations. They can also be used to easily break simple passwords.

Because many less tech-savvy individuals are unaware of the risks associated with choosing simple passwords, simple brute force attacks are still effective. Some may decide not to bother remembering longer, more complicated passwords, preferring to take a chance on their security with easy ones. Use a reliable password manager if you’re experiencing problems remembering your passwords.
Dictionary attacks
Dictionary attacks use a wordlist or digital dictionary as a tool to target increasingly difficult passwords. Choosing a password with a more difficult-to-guess term will protect you from basic brute force attacks, since most hackers will give up quickly. However, employing more difficult or esoteric terms won’t protect you from dictionary attacks.
Dictionary attacks cycle through every word, frequent word combinations with other words, spelling variants, and terms in different languages in an attempt to guess your password. A brute force dictionary attack will be successful in a matter of seconds if your password consists of only one word.
Hybrid brute force attacks
Dictionary attacks and basic brute force hacking techniques are combined in hybrid brute force assaults. To generate a more extensive database of password possibilities to try, dictionary words and common passwords are combined with random characters. While a password like “p@$$w0rd” could be able to thwart a dictionary assault, it would not be very effective against a hybrid attack.
Hackers that employ hybrid attacks will tailor their attack plan as opposed to testing each term one at a time. The infiltrator is aware of the most likely word combinations based on the target’s demographics, wordlists (perhaps obtained from the dark web), and general understanding of human behavior. They then order their attacks so that certain combinations are the first to be targeted.
Reverse brute force attacks
Reverse brute force attacks attempt to brute force the username rather than the password by starting with a well-known or common password. When passwords from data breaches do find their way online, they are frequently exploited to initiate reverse attacks.
Because so many people overlook security when choosing their login ID, brute force hacking usernames is more profitable than it may first appear.
Credentials stuffing
When a hacker manages to get their hands on your login and password for one website, they attempt to get in somewhere else using those same or nearly identical credentials. This is known as credential stuffing. Rather than attempting to crack a password or username, they are attempting to crack the location in which the password or username is utilized. You should never store passwords in your browser for this reason, among others.
Many of us use the same username and password on many websites, so if one of them is hacked, it doesn’t protect any of your accounts. Use different passwords for each of your accounts, but don’t forget to use antivirus software to strengthen your protection.
Avast One defends against a wide range of security risks, including viruses, dubious plugins, compromised passwords, and hazardous settings. Our integrated Smart Scan function will thoroughly examine your system, enabling you to quickly identify and address any vulnerabilities before they cause issues.
Tools used for brute force attacks
It takes a lot of time to manually try brute force attacks on all except the weakest passwords. However, in order to make password cracking easier, hackers have created a variety of automated methods, not all of which need trying every character combination.
Hackers typically employ the following instruments for brute force attacks:
- Ineffective techniques for targeting passwords
Hackers frequently avoid utilizing more complex techniques by employing systems that find and attempt the simplest, most obvious passwords first.
- WiFi decoys
Wi-Fi cracking tools gather information by analyzing Wi-Fi network security and utilizing it to launch more potent attacks against specific networks.
- Hashing algorithms
Hashing functions are algorithmic encryption techniques that generate lengthy, randomly generated passwords that can be deciphered by breaking tools.
- Dictionary automatic programs
Brute force techniques can quickly break single-word passwords through dictionary assaults.
Large volumes of data are processed quickly by all of these software applications, which requires a lot of processing power. Combining the CPU and GPU with specialized hardware tools for brute force is a common way to dramatically increase cracking speeds.
Why do cybercriminals use brute force attacks?
Brute force attacks are motivated by a variety of factors. Brute force assaults are frequently used by hackers and cybercriminals to infiltrate websites with more advertisements or to steal your personal information through phishing schemes. A website’s reputation can be ruined by a spiteful attacker using a brute force attack.
You can easily get a brute force password cracker on the internet. It is software that tries passwords repeatedly until it finds the one that works. That implies that anyone with some free time or a grudge can try it. As such, attacks will differ in their purpose and ferocity. However, strong brute force attacks have the ability to take over a system as a whole.
After going over some of the most typical forms of brute force attacks, let’s look at some of the motivations behind these tactics used by hackers.
The opportunity to explore hidden webpages
Attacks using brute force can uncover much more information than just users and passwords. An attacker can access directories or webpages that are normally hidden from public view by brute forcing web addresses.
Usually, these websites are set up for technical or private purposes, or they were made and then forgotten about. They might have less security than websites intended for the general public in both situations. They are probably more susceptible to malevolent threats, Trojan horses, SQL injections, and other harmful computer exploits.
A hacker may be able to obtain a trustworthy backdoor to the main website if they are able to brute force a hidden web page.
Profit from ads
Hackers can exploit unlawful access to websites to inundate users with advertisements, earning money from each click or view. Hackers can also divert traffic to fraudulent websites that are overflowing with advertisements or to pharming websites that are impersonated as legitimate ones.
Hackers can profit from spam by taking advantage of advertising business models and making users view and deal with endless advertisements.
Spread malware
Viruses and other malware are frequently distributed throughout a system using brute force attacks. The kind of software a hacker uses will determine whether or not they can access private information like your contact list and location.
A hacker can make money by infecting your device with adware, which allows them to continuously show you advertisements. Additionally, hackers have the ability to brute force a website and then infect everybody who views it with malware.
You may be protected against unforeseen risks with Avast One. While you browse the web, our Web Shield will prevent known malware from downloading to your computer, and our File Shield will scan unfamiliar files before they reach you, quarantining them right away if they contain hazardous content.
This implies that harmful attacks will be prevented from reaching your computer by Avast One, even if they originate from trusted domains that were inadvertently compromised by a brute force attack.
Furthermore, by continuously checking all of your settings and add-ons for any vulnerabilities, our integrated Smart Scan function will strengthen any gaps in your online security.
Do you require even more specialized defense against brute force attacks? Take a look at Avast Premium Security, which uses our integrated Remote Access Shield to automatically prevent brute force attempts on your device.
Steal data
Hackers can track user surfing data and sell it to third parties by getting access to websites. Advertisers looking to sell you products, analytics firms helping websites optimize their business models, and data brokers looking to sell individual or aggregated data to potential customers all value the information you provide.
For an unlucky hacker, downloading and utilizing a brute force password cracker is so easy that there is minimal risk involved. These days, big data equals large revenues.
Naturally, the person who takes your data can also utilize it for their own gain. For instance, a hacker may employ a brute force assault to install spyware and gather personal information for identity theft or doxxing.
Hijack systems
Hackers may first use brute force to get access, then infect your device with ransomware to either lock you out of your device entirely or take your important files hostage. Once they have gained control, hackers may threaten to delete your data or divulge private information in an attempt to coerce you into sending them money.
Petya and Wannacry are examples of ransomware that can lock your files until you pay, and even then there’s no assurance that your data will be restored.
How to defend against a brute force attack
Your first line of defense against a brute force assault is to use a safe password. Create different passwords for every account you have, and use a reliable password manager to keep them safe.
By restricting the number of login attempts or utilizing CAPTCHA and other comparable technologies to verify a user’s identity, Google and other services aim to thwart brute force assaults. The most recent versions of brute force attack software, however, can get around these defenses.
A hacker can attempt as many offline account log-ins on different devices if they know the password’s hash function. Hackers can also attempt to log into thousands of websites until they find a match, at which point they can return to try the initial target, since many people have a tendency to use the same username and password for many sites.
However, there are several things you can do on your own to stop brute force assaults, like adopting online security tools, enabling multi-factor authentication, and creating stronger password habits.
Use long, complex, and unique passwords
A longer password is preferable. Since having to reset your password is so unpleasant, a lot of us use the same one across several websites. We also frequently use short passwords. A secure password manager, which will generate and store passwords for you automatically, can help you avoid this issue and build difficult-to-crack passwords.
It is safer to use complex passwords than simple ones. Websites may have lately asked you to create a strong password. These lengthy, intricate passwords will be made up of any character, number, and symbol combinations. Password security is greatly increased by employing unique word or letter combinations and making your passwords longer.
Steer clear of common identifiers like your city’s name, your favorite sports team, or any other information that might be readily discovered by searching for your location or other demographic information. Additionally, make a fresh password for every account you have.
There are over eight billion possible combinations for a seven-letter password, thus brute force assaults can still be used. When you double that to 14 letters, the number of options skyrockets to 64 quintillion, which is more than there are sand grains on Earth. You can create more possible combinations with a jump of 21 letters than there are stars in the known universe.
Employee multi-factor authentication
You are required to use at least two separate forms of credentials to log in using multi-factor authentication (MFA) and two-factor authentication (2FA). These variables may consist of knowledge-based elements like a security query. Make sure not to select queries whose responses are readily available on your social media profiles.
By choosing 2FA under your security settings and verifying your identity via an SMS or authentication app, you can easily set up 2FA on Facebook or Google.
One-time objects that you must have with you at the time of log-in may likewise be used as criteria. A specialized authentication app, push notifications containing unique codes, or an email-based one-time password are a few examples.
A biometric identifier and like a fingerprint scan or facial recognition software, can be used as a third authentication element. Even with tremendous difficulty, it is not worth the effort unless you are a very valuable target for dedicated hackers to replicate or steal this information.
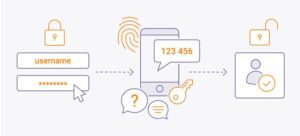
Beyond your password, multi-factor authentication provides other layers of protection (such as a PIN or biometric identifier). Also check Cloud computing companies
Strengthen your defenses
A good program can sometimes be the finest counterbalance to a malicious one. Using a VPN gateway or putting your network or website behind a firewall can provide an additional layer of protection against brute force methods.
Your system’s cracks and crevices can be secured by antivirus software. Modern defensive software is essential, and the finest antivirus systems update their software frequently with the newest techniques to prevent infections and hacker attempts.
Stand against brute force attacks with Avast One
Businesses must innovate to stay competitive with fearless hackers. An integrated function of Avast One searches the dark web for any evidence of your email address and linked personal information. Additionally, it will keep an eye on your password to make sure it hasn’t been compromised and notify you if it has, so you should update it.
Fortunately, brute force attacks don’t directly target most of us. Instead, hackers utilize brute force to get access to websites in order to distribute malware to users.
In order to prevent viruses and other malware from infecting your computer, Avast One will automatically block and delete malware from compromised websites, even ones that are typically safe. Additionally, we’ll shield you from dangerous email attachments, contaminated links, and harmful downloads.
It is important to have an additional layer of security to safeguard your data and other sensitive information because there are so many threats out there. To stay ahead of the hackers, download Avast One right now.